Topic last updated—March 2008
Microsoft System Center Configuration Manager 2007 provides a solid foundation for securely managing client to server communication on the intranet and over the Internet. However, there are many different methods by which attackers can attempt to penetrate your network. The use of IPsec is a common mitigation against many different types of attacks. Configuration Manager 2007 will work in an IPsec environment, and should be used when you are concerned about the risk of attackers intercepting, monitoring, or tampering with network communications.
IPsec allows you to maintain a high level of control over communications security. However, to effectively configure, manage, and troubleshoot IPsec policies, you must have an advanced knowledge of IP networking, experience with administering firewalls and filtering routers, and experience using network tools. This document assumes a working knowledge of general IPsec design and implementation.
For more information about server and domain isolation using IPsec and Group Policy, see http://go.microsoft.com/fwlink/?LinkId=93073 on the Microsoft Download site. Additionally, see a case study in IPsec deployment as well as lessons learned in the technical whitepaper at http://go.microsoft.com/fwlink/?LinkId=93074.
Interaction between IPsec and the Supporting Infrastructure
Configuration Manager 2007 requires the use of many standard services provided by the Windows operating systems. These services include name resolution, DHCP, RRAS, Volume Shadow Services, and other basic services required to operate in a secure networked environment. Carefully consider these services and their use within the Configuration Manager environment as you establish your IPsec policies.
Communication Paths
There are three primary Configuration Manager communication paths you should consider protecting with the help of IPsec.
- Site-to-site communication
- Site-to-site system communication
- Client-to-site-system communication
Site to Site Communication
Site to site communication occurs for two different scenarios:
- Site to site data replication
- Secondary site push installation
Site to site data replication occurs when data is exchanged between sites that are configured in a hierarchy as parent/child sites. Status messages, inventory data, and state messages flow up from child site to parent site. Software distribution packages, software updates, network access policies, operating system deployment images, task sequences, configuration baseline assignments flow down from parent site to child site. While these communications are signed by Configuration Manager 2007, they are not encrypted unless you enable IPsec.
If you install a secondary site from the Configuration Manager 2007 console of the parent primary site, the files are not encrypted unless you enable IPsec. IPsec between a primary site and a secondary site that is being installed helps secure the initial bootstrap communication process, including any configuration data sent from the primary site to the secondary site.
Site Server to Site System Communication
Site to site system communication encompasses three major functions:
- Initial provisioning of the site system
role
- Configuration of the services
- Transfer of configuration, status and
operations data
Initial provisioning of site systems services occurs using remote procedure calls (RPC) and transfers data using server message block (SMB). Although native mode signs policy using the site server signing certificate, mitigating some attacks against site server to site system communication, these communications are not secured in either mixed or native mode. You should enable IPsec to help protect site server to site system communications, especially if your site systems are placed across a security boundary, such as between Active Directory forests, or between a perimeter network and your intranet.
IPsec helps protect against attacks where an unauthorized site system impersonates a valid site system and uses the trusted connection to gain control of the site server or the site system database.
Client to Site System Communication
If your Configuration Manager 2007 site is operating in native mode, Configuration Manager 2007 uses Internet Information Services (IIS) to establish a secure connection over SSL between the client and some site systems, including the management point, but other communication is not encrypted, such as connections to the fallback status point. When your site is operating in mixed mode, only some communications are encrypted. The only way to be sure all client communication to site systems is signed and encrypted in all modes is to use IPsec.
For more information about how mixed and native modes use HTTP and HTTPS, see Client Communication in Mixed Mode and Native Mode.
 Note Note |
|---|
| Do not configure IPsec policies for the AMT communication between the out of band service point site system server and computers that will be managed out of band. |
IPsec Policy Configuration
It is recommended that you create an IPsec policy that requires ESP/3DES between the specified end points (site servers, site systems, clients). Packet layer encryption adds CPU load to these systems, so it is also recommended that you ensure proper lab performance testing of the configuration before deployment. Limit access to the specified site systems by limiting the computers that can be authenticated by IPsec Internet Key Exchange (IKE) with the Configuration Manager IPsec policy. You can also limit access to systems by using certificate authentication from a Certification Authority (CA) that is dedicated only to the purpose of issuing certificates for use with Configuration Manager IPsec.
Use the port information provided in the topic Ports Used by Configuration Manager to construct network traffic maps depending on the server role configuration on each computer participating in your site. Client roles are also shown in case you plan to use IPsec for encrypting client communication to site systems, or in case you are running the Configuration Manager 2007 client on site systems and need to permit the necessary traffic.
 Note Note |
|---|
| An update to Windows Server 2003 and Windows XP is available to help simplify the creation and maintenance of IPsec filters. For more information, see http://go.microsoft.com/fwlink/?LinkId=93076. |
IPsec to Domain Controllers
There are additional considerations with configuring IPsec on domain controllers, which could impact your Configuration Manager 2007-related IPsec policies if you host your site roles on domain controllers. For more information about configuring IPsec between Windows Server 2003 member servers and Windows Server 2003 domain controllers, see http://go.microsoft.com/fwlink/?LinkId=93078.
Site Servers with Client Components Installed
In configurations where the site systems configured for IPsec also have the Configuration Manager 2007 client agent installed and configured for native mode, you can modify the filter to permit HTTP and HTTPS traffic for Configuration Manager 2007 communications, and ICMP traffic for diagnostics. The recommended way to implement this configuration is to use a Group Policy that contains the IPsec policy.
Common Deployment Network Diagram for Internet-Based Servers
This scenario represents a Configuration Manager 2007 site that doesn't support intranet clients and spans the perimeter network and intranet. All the Internet-based site systems are in the perimeter network, and accept connections for clients connecting over the Internet. The site server and site database server are the intranet. The management point that supports Internet-based client communicates with a replica of the site database in the perimeter network.
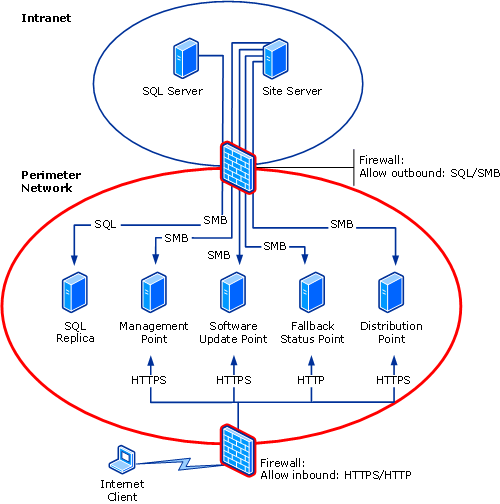
This common scenario follows a standard server isolation configuration. In this configuration, the connection between the site server and site systems, as well as the connection between the site database and the management point, should be configured with subnet based IPsec filters. If you use subnet-based filters and do not require the ability to support inbound sessions that are not encrypted with IPsec, you can use an “Any <-> subnet” IPsec policy design. You can use either Kerberos or computer certificate authentication. Computer certificate authentication is recommended, but the deployment of the computer certificates requires additional administrative overhead and is not managed by Configuration Manager 2007. Firewalls between sites and site systems should be configured to allow ISAKMP traffic (UDP Port 500) and UDP Port 4500 if you are using NAT traversal through the firewall.
The recommended IPsec policy for this configuration is:
- IP filter list:
- Source Address <any IP address>
- Destination Address <your subnet>
- Source Address <any IP address>
- Filter Action: - set to Do not allow
unsecured communication
- Authentication Methods: set to Use a
certificate from this certification authority (CA)
Other settings in the policy should be set according to your company standards.





