Prestaged clients are computer account objects that are created within Active Directory Domain Services (AD DS) before the operating system is installed. They correspond to physical devices that will boot from the network by using Windows Deployment Services.
In This Topic
How Prestaged Clients Are Located
When a client computer attempts to boot from the network, limited data is transferred from the client to the server as part of the Pre-Boot Execution Environment (PXE) protocol. Windows Deployment Services can locate prestaged clients by using either of the following:
- GUID (recommended). A computer's GUID
is a unique 32-character hexadecimal value supplied by the
manufacturer of the computer that is stored within the system BIOS.
The GUID format occurs in two formats:
- String format (also known as wire format).
Example: 0123456789ABCDEF0123456789ABCDEF
- Display format. Example (using the same GUID
as the first bullet):
{67452301-AB89-EFCD-0123-456789ABCDEF}
- String format (also known as wire format).
Example: 0123456789ABCDEF0123456789ABCDEF
- MAC address. The MAC address is a
128-bit hardware address that uniquely identifies each node of a
network. The first part of the address is unique to the company
that produced the device and is a sequence of digits that are
unique to a device manufactured by that company.
The following is the Lightweight Directory Access Protocol (LDAP) search filter used by Windows Deployment Services: (&(objectCategory=<DN of Computer Schema object>)(|(netbootGUID=<GUID>)(netbootGUID=MAC))). This filter ensures that a device will be found if it is prestaged using either a computer GUID or a MAC address. The netbootGUID attribute on a prestaged client is used to store the value of the physical computer’s GUID or the MAC address. You can use the Ldp GUI tool to view this value.
When a PXE request is submitted, it contains both of these values in the DHCPREQUEST packet. The computer's GUID is in the Dynamic Host Control Protocol (DHCP) options (tag 97 in DHCP options), and the MAC address is in the Ethernet Source Address part of the packet. The PXE server forwards the PXE request to the Windows Deployment Services server. The server extracts both pieces of information, binds against an AD DS server, and searches for a match on either value. If a match is found, the client is considered known. If no match is found, the client is considered unknown.
The following are three scenarios in which the booting device will not be uniquely identified and the server will return an error:
- Two computers are found in AD DS with
the same computer GUID.
- Two computers are found in AD DS with
the same MAC address. For example, if you prestage the MAC address
of Server1, then you build and prestage Server2 by using the
network adapter from Server1. Now you have two prestaged devices in
AD DS with the same MAC address.
- Two devices in AD DS represent a single
physical computer — one device prestaged with a computer GUID, and
the other one prestaged with a MAC address.
When Prestaged Clients Are Joined to a Domain
If a client computer is prestaged in AD DS, the client will be joined to the domain as the prestaged device. You can override this by running the /JoinDomain:No command on the command line (for example, WDSUTIL /Set-Device /Device:Computer2 /User:Domain\user /JoinRights:JoinOnly /JoinDomain:No). If a client computer is not prestaged, the per-server policy settings dictate the domain join behavior (for example, the computer name and location in AD DS). In all cases where Windows Deployment Services creates a computer object to facilitate the domain join process, the account that is created will contain either the client's GUID or MAC address (as stored in the netbootGUID attribute). This automatic prestaging is beneficial because if you rebuild a computer (for example, from a failed hard disk drive), the computer will be joined to the same domain using the same computer name.
For instructions on setting these options, see the “Prestage Computers” section in How to Manage Client Computers (http://go.microsoft.com/fwlink/?LinkID=115265).
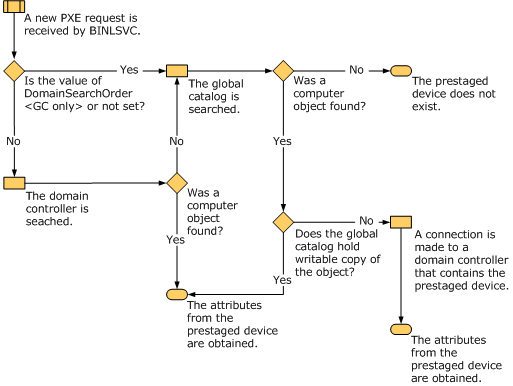
Diagram of Prestaging Clients
The following flowchart shows the connections that the Windows Deployment Services PXE provider (BINLSVC) will make to locate a prestaged device and read its attributes.
Examples
The following example cases outline the Windows Deployment Services search behavior, depending on your configuration. Note that you would run WDSUTIL /Set-Server /DomainSearchOrder:GCOnly (also the default configuration) to search global catalogs first and then search domain controllers. Conversely, you would run WDSUTIL /Set-Server /DomainSearchOrder:DCFirst to search domain controllers first and then search global catalogs.
| Scenario | Result |
|---|---|
|
Case A /DomainSearchOrder:GCOnly |
BINLSVC connects to global catalog-A. The object is not found, which means that either the device has not been prestaged or AD DS replication latency has caused the device not to replicate to that global catalog. No further action is required by BINLSVC. Result: BINLSVC connected to one server. |
|
Case B /DomainSearchOrder:GCOnly |
BINLSVC connects to global catalog-A. The object is found. Global catalog-A also contains a writeable copy of the prestaged device object in its domain controller partition. AD DS attributes are read from there. Result: BINLSVC connected to one server. |
|
Case C /DomainSearchOrder:GCOnly |
BINLSVC connects to global catalog-A. The object is found. Global catalog-A does not contain a writeable copy of the prestaged device object in its domain controller partition. Therefore, BINLSVC must connect to domain controller-B to read the additional Windows Deployment Services attributes from the computer object. Result: BINLSVC connected to two servers. |
|
Case D /DomainSearchOrder:DCFirst |
BINLSVC connects to domain controller-B. The object is not found. BINLSVC connects to global catalog-A to determine whether the object exists in the forest. The object is not found. Result: BINLSVC connected to two servers. |
|
Case E /DomainSearchOrder:DCFirst |
BINLSVC connects to domain controller-B. The object is not found. BINLSVC connects to global catalog-A to determine whether the object exists in the forest. The object is found. Global catalog-A also contains a writeable copy of the prestaged device object in its domain controller partition. AD DS attributes are read from there. Result: BINLSVC connected to two servers. |
|
Case F /DomainSearchOrder:DCFirst |
BINLSVC connects to domain controller-B. The object is not found. BINLSVC connects to global catalog-A to determine whether the object exists in the forest. The object is found. Global catalog-A does not contain a writeable copy of the prestaged device object in its domain controller partition. Therefore, BINLSVC must connect to domain controller-C to read the additional Windows Deployment Services attributes from the computer object. Result: BINLSVC connected to three servers. |
|
Case G /DomainSearchOrder:DCFirst |
BINLSVC connects to domain controller-B. The object is found. BINLSVC reads additional Windows Deployment Services attributes from domain controller-B. Result: BINLSVC connected to one server. |