The base environment for centralized management consists of at least two domain controllers and one server that serves as a Web server. This is illustrated in the following figure.
Any scenarios involving multiple sites and domains will increase the number of domain controllers and domains in the system.
You may already have a network, perhaps one that is fairly complex, with outside and inside firewalls separating demilitarized zones and core networks, and an existing DNS implementation. In this case there is no point in building a completely separate network for your hosting environment, you can use the network you already have.
Read more about planning for two or more directory servers
We recommend that you use at least two Active Directory servers, to make use of the built-in redundancy and reliability features in Active Directory.
Consider the impact on your business if you use a single Active Directory server and it fails. Internet surfers will be able to access your customers' sites, but neither you nor your customer will be able to manage their services or add new customers. Restoring your directory from a backup-if a backup is available-requires significant time and difficulty. This downtime equates to lost revenue and customers.
Using at least two Active Directory servers eliminates this problem. The Active Directory servers use automatic replication to keep accounts and configuration information synchronized. This means that either server can become the single source of all directory information on your network, at any time If one server fails, you can quickly add a replacement server to the network and promote it to be a domain controller. The existing domain controller will begin replicating the directory tree to the new server with no service downtime.
Network Zones
The definition of zones in are:
- Zone 0 - "Boundary"
- The area of the network is closest to the Internet. Generally
this security zone contains the boundary routers, intrusion
detection, first layer of denial of service (DoS) blocking, and
boundary firewalls.
- Secure Sockets Layer (SSL) and initial access/certificate
validation may be located at this layer. NOC (Network Operation
Center) services may be logically housed in this zone.
- For Hosted Messaging and Collaboration version 4.5, no solution
servers in this zone.
- The area of the network is closest to the Internet. Generally
this security zone contains the boundary routers, intrusion
detection, first layer of denial of service (DoS) blocking, and
boundary firewalls.
- Zone 1 - "Edge"
- This zone contains those servers and services that provide
first level authentication, load balancing across Zone 1 servers
and services.
- No domain membership with the Zone 3 Active Directory and no
direct connection to servers in Zone 3 for security purposes. This
reduces the attack surface.
- A "Secure by Default" approach - locked down servers in this
zone.
- Communication via secure protocols between servers in Zone 1
and Zone 2.
- This zone contains those servers and services that provide
first level authentication, load balancing across Zone 1 servers
and services.
- Zone 2 - "Proxy"
- Servers in this zone have domain membership with Active
Directory in Zone 3.
- Relays or "proxies" authentication requests between Zone 1 and
Zone 3.
- Servers in this zone have domain membership with Active
Directory in Zone 3.
- Zone 3 - "Datacenter"
- Most secure area of the network.
- Data repository servers reside in this zone.
- No direct access to these servers’ access is via proxies in
Zone 2.
- Most secure area of the network.
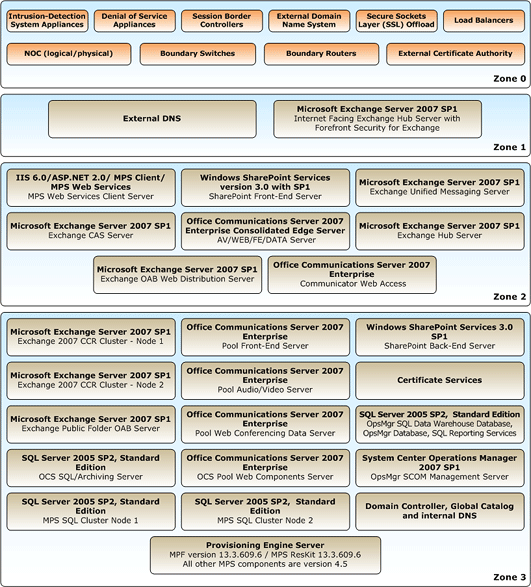
Figure: Network reference architecture