Previous versions of the reference architecture for specified a flat, single tiered deployment, consistent with and optimized for the messaging component based on Microsoft Exchange Server 2003.
With the upgrade to Microsoft Exchange Server 2007 Service Pack 1 in Hosted Messaging and Collaboration, the reference architecture has transitioned from the flat network design to a three-tiered, four-zone approach. This approach to networking has been used by telecommuncation companies for data services to reduce the attack surface and secure data access.
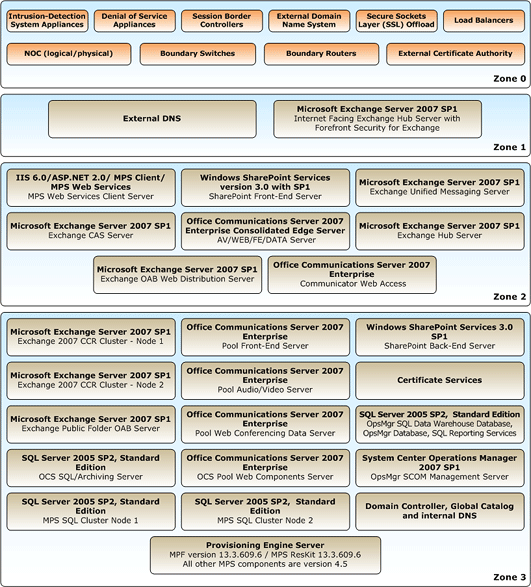
Figure: Network reference architecture
The zones are as follows:
- Zone 0 - "Boundary"
- The area of the network that is closest to the Internet.
Generally, this security zone contains the boundary routers,
intrusion detection, first layer of denial of service (DoS)
blocking, and boundary firewalls.
- Secure Sockets Layer (SSL) and initial access/certificate
validation may be located at this layer. Network Operation Center
(NOC) services may be logically housed in this zone.
- For Hosted Messaging and Collaboration, no solution servers in
this zone.
- The area of the network that is closest to the Internet.
Generally, this security zone contains the boundary routers,
intrusion detection, first layer of denial of service (DoS)
blocking, and boundary firewalls.
- Zone 1 - "Edge"
- This zone contains those servers and services that provide
first level authentication, and load balancing across Zone 1
servers and services.
- No domain membership with the Zone 3 Active Directory service
and no direct connection to servers in Zone 3 for security
purposes. This reduces the attack surface.
- A "Secure by Default" approach. Locked down servers in this
zone.
- Communication via secure protocols between servers in Zone 1
and Zone 2.
- This zone contains those servers and services that provide
first level authentication, and load balancing across Zone 1
servers and services.
- Zone 2 - "Proxy"
- Servers in this zone have domain membership with Active
Directory in Zone 3.
- Relays or "proxies" authentication requests between Zone 1 and
Zone 3.
- Two tier services to publish secure application access in lieu
of a dedicated Zone 1 or edge server.
- Servers in this zone have domain membership with Active
Directory in Zone 3.
- Zone 3 - "Datacenter"
- Most secure area of the network.
- Data repository servers reside in this zone.
- No direct access to these servers. Access is via proxies in
Zone 2.
- Most secure area of the network.