This section documents the alternative Active Directory design options, including additional Active Directory models, which could be used in a solution. However, the only Active Directory design that the Test team has tested is the recommended single-forest, single-domain model, which is directly supported by MPS.
Active Directory Logical Models
There are five alternative logical models for Active Directory.
As shown in the following figure, the first two single-forest, single-domain models are similar, except for the differences in their OU structures, which are shared or dedicated. Each is listed separately due to the shared aspect of the model as covered in the reference architecture.
- Single-forest, single-domain - Shared
- Single-forest, single-domain - Dedicated
The next three logical models may be appropriate when a hosting company branches out to provide enhanced higher-margin managed hosted services, such as Microsoft Exchange, e-commerce, database hosting, Active Directory-enabled applications, and higher-end applications hosting.
- Single-forest, multiple-domains
- Multiple-forests - Super Admin domain
- Multiple-forests - Super Admin forest
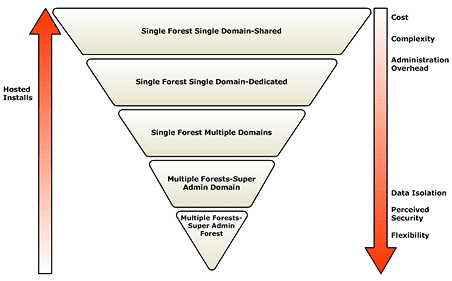
The preceding figure and the following list illustrate a number of business reasons that may affect the decision to adopt one of the Active Directory logical models.
- Cost - A single-forest, single-domain model requires the
fewest number of Active Directory domain controllers, assuming
everything else is equal.
- The recommended model requires at least two Active Directory
domain controllers. This allows for a minimum amount of redundancy
required to support Active Directory services. If you require a
2N+1 level of redundancy, you can add an additional domain
controller as required.
- If you add additional domains and multiple forests, the minimum
number of servers for deployment increases linearly. However, when
the minimum operational staffing threshold is reached in a
well-run, highly-scalable data center, the operational cost per
additional server is minimized. You can achieve this level of
efficiency by establishing mechanisms to automate deployment and
operational processes.
For example, the number of operational and system administration staff required to support the Microsoft Hotmail Web-based e-mail service has not increased since before June of 2000, when Microsoft Windows 2000 Server and IIS 5.0 were implemented to support the front-end Web services. This statistic is noteworthy when you consider that the number of e-mail subscribers has increased from approximately 50,000,000 at that time, to over 106,000,000 now, and the number of Web servers has increased from 3,200 to 5,200.
- The recommended model requires at least two Active Directory
domain controllers. This allows for a minimum amount of redundancy
required to support Active Directory services. If you require a
2N+1 level of redundancy, you can add an additional domain
controller as required.
- Complexity - Clearly the single-forest, single-domain is
the simplest model to deploy and manage. As a service provider
moves down to the more advanced models, complexity
increases.
- Administration overhead - As you move to more advanced
models, administrative complexity increases. Multiple forest models
add the overhead of manually managing trust among the forests,
although you can automate the management of trust relationships. By
deploying centralized management on your user accounts and server,
you minimize this cost.
- Data isolation - The global catalog in Active Directory
is a special type of domain controller that contains a copy of all
objects that exist within a forest boundary. By implementing the
multiple forest models, data can be isolated within forest
boundaries. In other words, the domain is not a security boundary
in Active Directory because the global catalog is a common
collection of data across domains. There may be security
environments where this is not acceptable. In these cases, a
multiple forest model provides total isolation.
 Note:
Note:The single-forest, single-domain model prescribed in the solution effectively protects against cross-customer data browsing through the delegated administration security model. - Perceived security - If configured and managed
correctly, each of the Active Directory models is secure. Strong
policies for passwords and accounts can also be implemented in the
single-forest, single-domain model. If the single-forest,
multiple-domain model is implemented, these policies can be
strengthened because the policies for passwords and accounts are
maintained at the domain level. The multiple-forest models are
totally isolated and thus are secure by default, while the
single-forest, single-domain model has potential for
cross-container viewing of data, if the proper security policies
are not maintained.
- Flexibility - Certain features of Active Directory are
tied to different boundaries within the directory, that is, the
forest, domain, OU, or site. Implementing the single-forest,
multiple-domain model or multiple-forest models allow the service
provider greater flexibility. For example, the Active Directory
schema is forest-wide. If there are requirements for custom schema
changes, the use of multiple forests may be required to isolate
such changes from the entire directory.
The domain models differentiate between the forest, tree, domain, and, to some degree, site levels as boundaries. Regardless of which domain model you are using, the reference architecture recommends that the service provider maintain the same OU structure for practicality and ease of administration. If the OU structure is the same across domains, then there can be consistency in administration, management, and operation of the domains using common tools and processes.