 Advanced
Configuration
Advanced
Configuration Operations Monitor
2.0 Default Configuration File
(PMonitor2_0.default.config)
Operations Monitor
2.0 Default Configuration File
(PMonitor2_0.default.config)By default, when Intercept uX is configured for monitoring in
Full Mode, AJAX calls will be distinguished from other calls on the
server side. If uX monitoring is disabled or configured for
Statistical Mode however, is still possible to distinguish AJAX
calls on the server side. Please see please see AVIcode Intercept Studio User
Manual  Advanced
Configuration
Advanced
Configuration Operations Monitor
2.0 Default Configuration File
(PMonitor2_0.default.config)
Operations Monitor
2.0 Default Configuration File
(PMonitor2_0.default.config)
For this section you may either use the Intercept uX Management Console, and edit the Data Collecting properties, or manually edit the uX configuration file. To access the file:
 Please note
that on x64 installation, the server agent and its associated
configuration files may be found under "Program Files ", while
other components will be under "Program Files (x86)"
Please note
that on x64 installation, the server agent and its associated
configuration files may be found under "Program Files ", while
other components will be under "Program Files (x86)"The disabledContent flag determines which content is disabled from collection. Default value = 63 (means that all are disabled). The flag's values may be set to:
Bitwise combination of these flags is also supported. For example:
In order to collect CSS, images and scripts, edit the file as in the following example:
Before:
|
<ss:appdomains
minorPageLoadTime="1000" majorPageLoadTime="10000" calcLinkedContentUsingAjax="true" collectHtc="false" include="false" includeStatistic="false" includeProblem="false" statisticsSampling="10" samplingMode="Statistics" scriptsVersion="" disabledContent="4"> ... |
After:
|
<ss:appdomains minorPageLoadTime="1000" majorPageLoadTime="10000" calcLinkedContentUsingAjax="true" collectHtc="false" include="false" includeStatistic="false" includeProblem="false" statisticsSampling="10" samplingMode="Statistics" scriptsVersion="" disabledContent="0"> ... |
For this section you must manually edit the uX configuration file. To access the file:
 Please note
that on x64 installation, the server agent and its associated
configuration files may be found under "Program Files ", while
other components will be under "Program Files (x86)"
Please note
that on x64 installation, the server agent and its associated
configuration files may be found under "Program Files ", while
other components will be under "Program Files (x86)"By configuring the path to tenant variable in the HttpContext, Intercept uX will extract it while monitoring, and pass the internal business context to both the uX and server agent events.
When updating the configuration file to include tenant information, be sure to set the value of "tenantPathCount" to the number of tenant paths being added as in this example:
|
<ss:dataProviderSettings> ... <ss:add name="tenantPathCount" alias="tenantPathCount" value="2" include="true" /> <ss:add name="tenantPath1" alias="test" value="1/System.Web.HttpContext::Request/System.Web.HttpRequest::Headers/System.Collections.Specialized.NameValueCollection" include="true" /> <ss:add name="tenantPath2" alias="test" value="1[Tenant_Header]/System.String " include="true" /> ... </ss:dataProviderSettings> |
Also note that the alias does not have to be unique, but the name of the tenant path does need to be unique:
|
<ss:dataProviderSettings> ... <ss:add name="tenantPathCount" alias="tenantPathCount" value="2" include="true" /> <ss:add name="tenantPath1" alias="test" value="1/System.Web.HttpContext::Request/System.Web.HttpRequest::Headers/System.Collections.Specialized.NameValueCollection" include="true" /> <ss:add name="tenantPath2" alias="test" value="1[Tenant_Header]/System.String " include="true" /> ... </ss:dataProviderSettings> |
Follow the appropriate sections below for examples of extracting tenant information from request headers, session variables or form variables.
In order to collect tenant information from the HTTP Request Header, edit the file as in the following example (assuming that Tenant is stored in the Request Header called “Tenant_Header”)
|
<ss:dataProviderSettings> ... <ss:add name="tenantPathCount" alias="tenantPathCount" value="2" include="true" /> <ss:add name="tenantPath1" alias="test" value="1/System.Web.HttpContext::Request/System.Web.HttpRequest::Headers/System.Collections.Specialized.NameValueCollection" include="true" /> <ss:add name="tenantPath2" alias="test" value="1[Tenant_Header]/System.String " include="true" /> ... </ss:dataProviderSettings> |
In order to collect tenant information from the HTTP SessionVariable, edit the file as in the following example (assuming that Tenant is stored as an element value (accepted by the key “current_network_id”) of a Hashtable located in a session variable called “Enterprise.ApplicationState” as a value (accepted by key “MemberContext.MEMBER_CONTEXT”)
|
<ss:dataProviderSettings> ... <ss:add name="tenantPathCount" alias="tenantPathCount" value="3" include="true" /> <ss:add name="tenantPath1" alias="test" value="1/System.Web.HttpContext::Session[Enterprise.ApplicationState]/System.Collections.Hashtable" include="true" /> <ss:add name="tenantPath2" alias="test" value="1[MemberContext.MEMBER_CONTEXT]/System.Collections.Hashtable" include="true" /> <ss:add name="tenantPath3" alias="test" value="1[current_network_id]/System.Object" include="true" /> ... </ss:dataProviderSettings> |
In order to collect tenant information from the HTTP Request Form Variable, edit the file as in the following example (assuming that Tenant is stored in a Request Form Variable called “Tenant_Form”)
|
<ss:dataProviderSettings> ... <ss:add name="tenantPathCount" alias="tenantPathCount" value="2" include="true" /> <ss:add name="tenantPath1" alias="test" value="1/System.Web.HttpContext::Request/System.Web.HttpRequest::Form/System.Collections.Specialized.NameValueCollection" include="true" /> <ss:add name="tenantPath2" alias="test" value="1[Tenant_Form]/System.String " include="true" /> ... </ss:dataProviderSettings> |
For this section you must manually edit the uX configuration file. To access the file:
 Please note
that on x64 installation, the server agent and its associated
configuration files may be found under "Program Files ", while
other components will be under "Program Files (x86)"
Please note
that on x64 installation, the server agent and its associated
configuration files may be found under "Program Files ", while
other components will be under "Program Files (x86)"Intercept uX provides ability to define the signatures of JavaScript functions whose runtime duration will be excluded from the duration of the monitored bounding (outer function) scope.
|
<ss:excludes> <ss:exclude name="window.alert" paramCount="1" isSystem="true" /> <ss:exclude name="window.prompt" paramCount="2" isSystem="true" /> <ss:exclude name="window.confirm" paramCount="1" isSystem="true" /> <ss:exclude name="your_function" paramCount="num" isSystem="false" /> </ss:excludes> |
Where:
your_function = your custom function name
num = the number of function parameters in your custom function
isSystem = a Boolean flag that should always be set to false for custom functions
For this section you must manually edit the uX configuration file. To access the file:
 Please note
that on x64 installation, the server agent and its associated
configuration files may be found under "Program Files ", while
other components will be under "Program Files (x86)"
Please note
that on x64 installation, the server agent and its associated
configuration files may be found under "Program Files ", while
other components will be under "Program Files (x86)"To Enable Click Events uncomment the following section
|
<!-- <ss:add controlTagName="input" eventName="onclick" eventAliasName=".OnClick()"/> <ss:add controlTagName="img" eventName="onclick" eventAliasName=".OnClick()"/> <ss:add controlTagName="a" eventName="onclick" eventAliasName=".OnClick()"/> <ss:add controlTagName="a" eventName="href" eventAliasName=".href-javascript:(...)"/> <ss:add controlTagName="td" eventName="onclick" eventAliasName=".OnClick()"/> <ss:add controlTagName="span" eventName="onclick" eventAliasName=".OnClick()"/> --> |
To enable two separate subnets for monitoring, add only one filter group that disables monitoring for everything except these two subnets. Therefore the system will check the condition “If User’s IP is not in subnet1 and User’s IP is not in subnet2" then disable monitoring.
![]() Start
Start
![]() Programs
Programs
![]() AVIcode Intercept Studio
AVIcode Intercept Studio
![]() Intercept Configuration
Intercept Configuration
![]() Intercept uX Management Console
Intercept uX Management Console
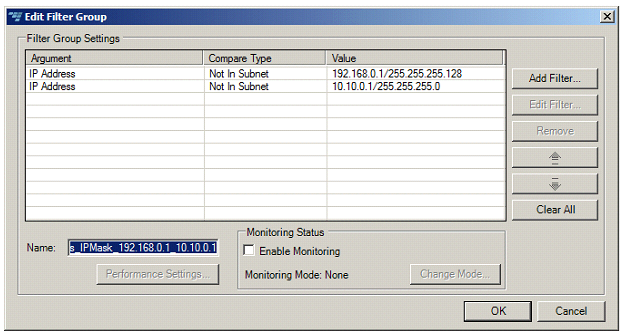
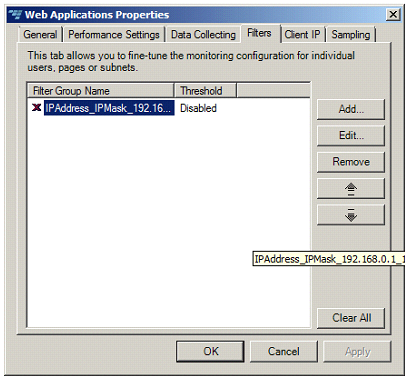
This section describes how to filter for particular client IP addresses in Intercept uX.
Filter groups allows configuring specific monitoring settings for specific types of pages and requests (based on selected parameters). Each filter group is comprised of several filters. Monitoring settings (thresholds, mode, etc.) are applied if a request/response satisfies all filters in the group.
Each filter has “action”, either "allow" or "deny" (Allow/Deny) attribute, meaning that settings are applied either to pages/requests whose parameters (page names, IP addresses, User name, tenant or other request and response parameters) match the filter (Allow), or to pages/requests whose parameters do not match the filter (Deny).
To add IP Filter Groups using the Intercept uX Management Console:
![]() Start
Start
![]() Programs
Programs
![]() AVIcode Intercept Studio
AVIcode Intercept Studio
![]() Intercept Configuration
Intercept Configuration
![]() Intercept uX Management Console
Intercept uX Management Console
Please note that the annotations on the screenshots refer to parameters in the CSM.action.config file.
Go to:
![]() Start
Start
![]() Programs
Programs
![]() AVIcode Intercept Studio
AVIcode Intercept Studio
![]() Intercept Configuration
Intercept Configuration
![]() Intercept uX Management Console
Intercept uX Management Console
Last update: Thursday, December 09, 2010 12:46:40 PM